Comprehensive Managed IT Security Services
Your business is at risk when assets are not sufficiently protected and security systems are not properly configured and managed. It’s essential for businesses today to have a comprehensive managed security service provider (MSSP). It costs less than in-house solutions, provides round-the-clock service, and always remains up-to-date. Most importantly, it allows your organization to focus on its core activities while remaining protected against threats and vulnerabilities.

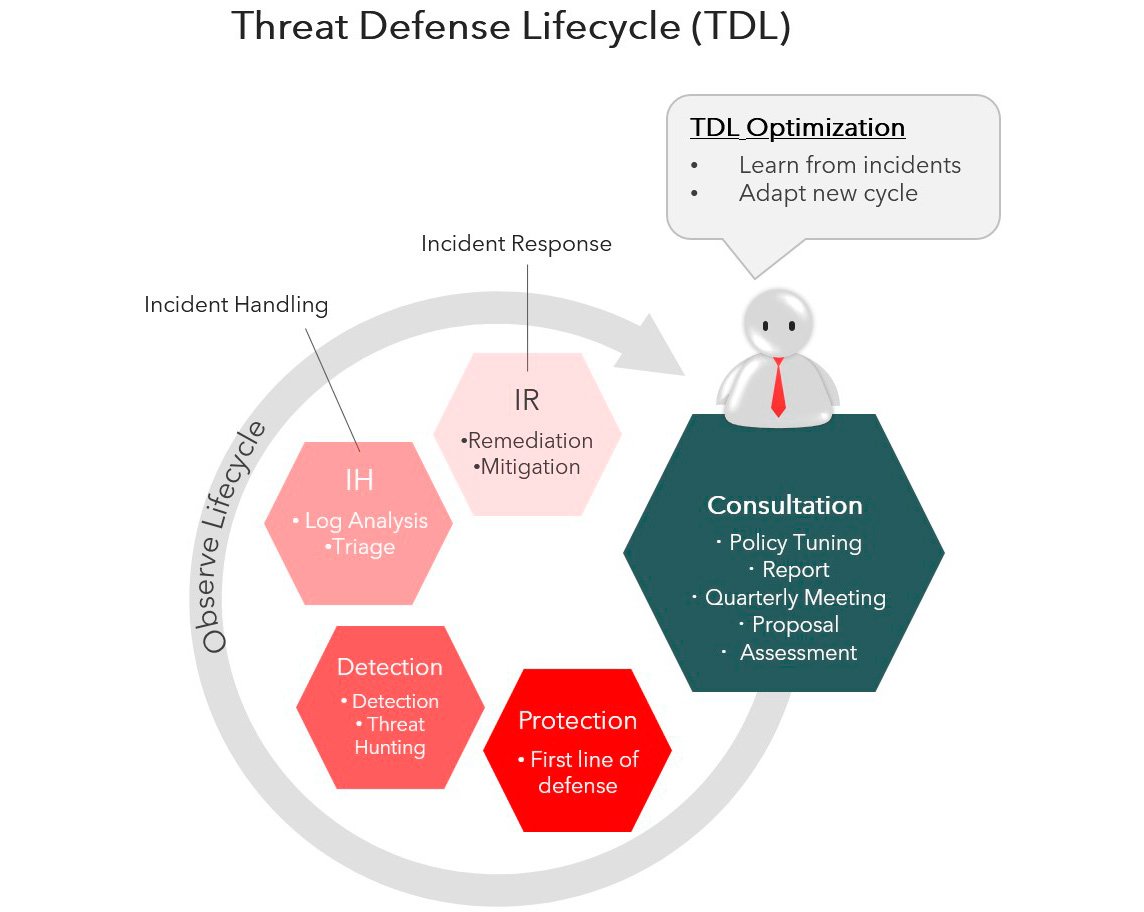
Threat Defense Lifecycle (TDL)
There are five important categories in our Threat Defense Lifecycle (TDL). When fully engaged with our TDL framework, businesses will be more secure and compliant with regulations. They will have access to experts who understand the most unique and leading technologies out there. And with such comprehensive protection, businesses can go back to focusing on their core activities.
Consulting
Protection
Detection
Incident Handling
Incident Response
Protect Your Business
Comprehensive security solutions help companies of all sizes keep every part of their business secure, trusted and worry-free. Our experts will be on your side to ensure your most important resources are protected and business risks are minimized.
We help protect your infrastructure, data, and people from external and internal security threats. Please contact us for more details.




