Practical Applications
SYSCOM GLOBAL SOLUTIONS’ Security Operations Center is on the frontlines of ever-changing cybersecurity threats and responses. As a service to our clients and partners, the Cybersecurity Minute provides updates on evolving cybersecurity threats, countermeasures, and security strategies they’re seeing and using in the course of their regular security work.
In our previous Cybersecurity Minutes, we explained common cybersecurity threats, then detailed a handful of basic, simple-to-implement cybersecurity measures companies can start putting into practice almost immediately to counter those threats. Here, we’ll show two different applications of those countermeasures: the Zero Trust Model and Information Leakage Countermeasures.
1. Zero Trust Model
Conventional cybersecurity measures set up a digital perimeter around a network to guard against external attacks and prevent intrusions into the internal network. However, as perimeter security models have improved, so too have cyberattacks adjusted to accommodate them, leading to more and more breaches. Recent cybersecurity solutions have shifted away from perimeter models to embrace the Zero Trust Model, one that makes no distinction between the external and internal.
The Zero Trust Model bases its defenses and countermeasures on exactly what it says: trusting nothing. Where conventional security measures divide the network into trusted internal areas and untrusted external areas and place countermeasures along the perimeter that divides these areas, Zero Trust treats internal networks as no more secure than external actors and develops a security strategy that doesn’t distinguish between the two.
The model assumes intrusions will occur and aims to minimize damage and limit exposure when they do. It visualizes threats and actions that could occur in a cybersecurity intrusion and designs appropriate countermeasures to engage and contain the threat as soon as possible.
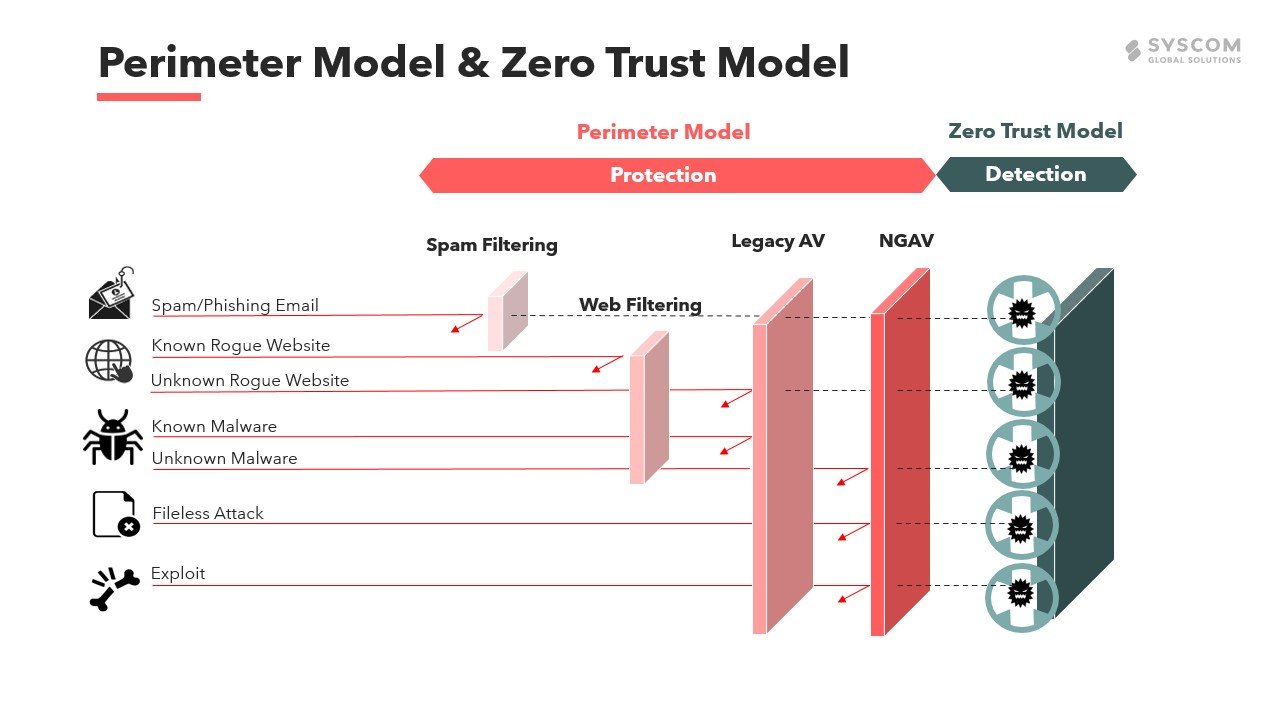
2. Information Leakage Countermeasures
Countermeasures against external cyberattacks are, of course, still necessary, but confidential information leakage due to internal factors, like employees removing data from a secure environment or making simple mistakes, can also cause security incidents. Demand for cloud security from a Cloud Access Security Broker (CASB) for remote work environments is subsequently increasing. A CASB monitors and controls usage of cloud services, no matter where or how they are accessed or connected. A CASB offers various services, like web filtering, communication control, access history analysis, and more.
Its most important function is Data Loss Prevention (DLP). For example, to limit the external sharing of confidential data, file uploads to cloud services outside an approved Microsoft 365 ecosystem, like Google Drive or iCloud, can be visualized and warned against. When uploading sensitive information to one of these platforms outside the approved ecosystem, users can be warned and IT can be alerted, better controlling the leak.
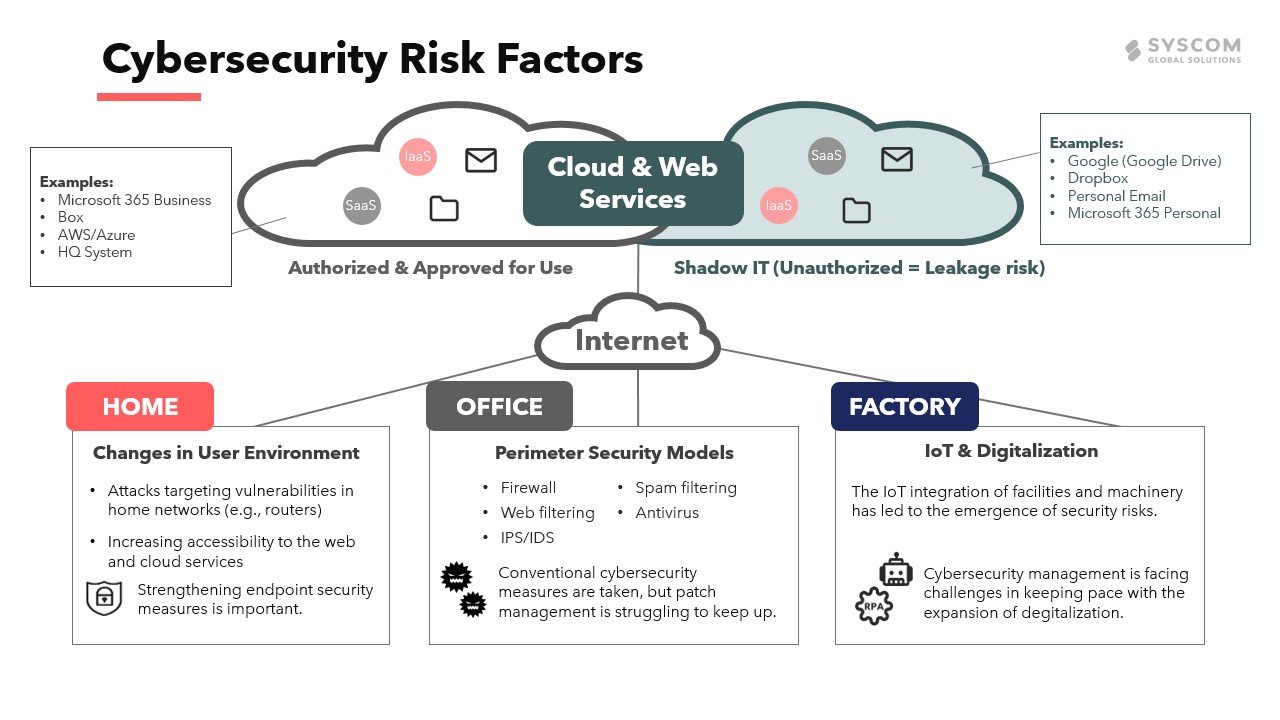
In situations like these, where the security incident isn’t caused by an external attack but rather by an internal employee removing data (intentionally or otherwise), such a warning system is necessary to limit such events.
In the modern, hyper-connected era, cybersecurity incidents are impossible to prevent entirely, even with everything described here implemented. However, by putting basic countermeasures in place, you can manage cybersecurity risk and significantly mitigate or contatin potential damage. Once these basic security measures have been taken, you can then add advanced security solutions as needed.
If you need help starting, reach out to us. SYSCOM specializes in providing security services for IT teams, and we’d be happy to schedule a consultation and propose a solution to fit your industry, working style, and company size.
News and Resources
Employee Spotlight: Hector Melo
How Hector Melo’s desire to keep growing sets the tone for SYSCOM. “You don’t stop learning at SYSCOM. You always learn something new.”
The differences and importance between OT Security and IT Security
In this article, we’ll explain the reason why OT security is so important and lay out steps and key points for successful OT security measures.
End of Hosting Service Announcement 12/31/2024
Thank you for using our Hosting service; however, we are announcing end of hosting services on 12/31/2024.



