Incident Response & Disaster Recovery
Incident response is the final piece of the threat defense lifecycle and is the methodology used to respond and manage cyberattacks quickly to accelerate the speed of disaster recovery. These attacks or data breaches can wreak havoc on your business, intellectual property, time, resources, and brand value. Our incident response team limits the damage in the shortest time possible, handles critical security incidents, and conducts analysis to resolve immediate and future cyberattacks.

Approach
Our incident response team combines cutting-edge security tools and human expertise to identify attackers quickly, implement provisional measures such as containment, and eliminate them from your environment. The most effective incident response can limit the impact of an event, accelerate the speed of disaster recovery and reduce the cost of a security breach.
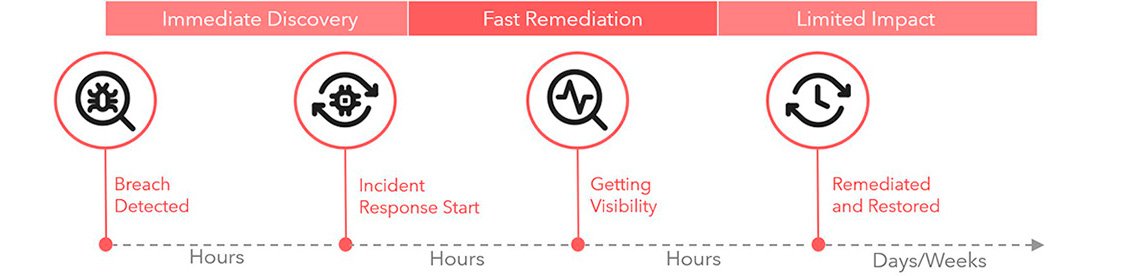
Flow
Our incident flow delivers an effective incident handling and response. We will identify each specific threat to determine whether an alert is a true threat and immediately assess the damage.
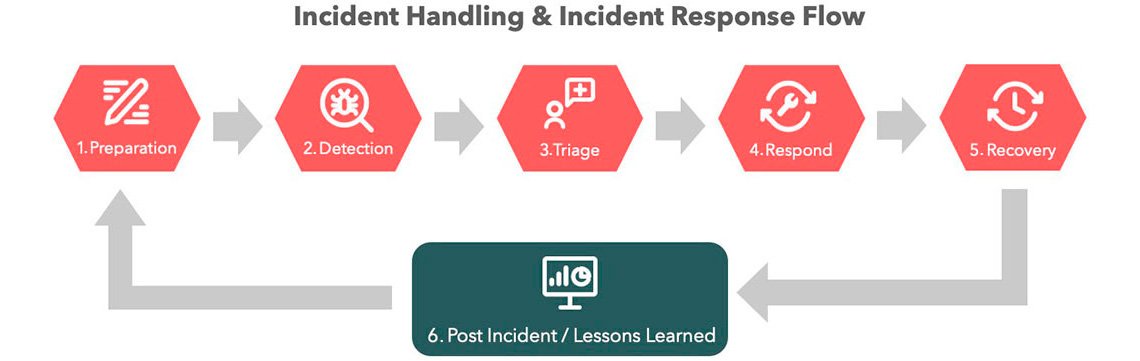
What We Offer
1.Preparation
Preparation is the key to a successful incident response. We will pre-determine the guidelines and our incident response team will effectively address a security incident.
2.Detection
We utilize the leading technologies and tools to monitor security events in order to better detect alerts on suspicious activities on data, devices, and services.
3.Triage
We will perform alert triage to quickly identify if an alert should be dismissed or escalated and then we further analyze the data collected from our tools and systems. This gives our experts a definitive understanding of what happened and when, who was affected, the extent of the attack, and how critical. With this information, we can plan the most effective response.
4.Response
With the analytical reviews and identification of threats, we recommend the best way to contain and remediate each threat. Our experts will determine whether to isolate a system from the network.
5.Recovery
The final step in our security approach is recovery. If this step is not performed properly, your organization’s entire investment in security tools will be for nothing. Our expertly managed recovery/remediation restores systems back to normal preventing further compromise.
6.Post Incident Activity
With the security threats contained and eradicated, our security operations team uses what we’ve learned to complete an incident report and identify preventative measures, such as policy tuning, configuration changes, and updating threat intelligence to prevent future incidents.
Protect Your Business
Comprehensive security solutions help companies of all sizes keep every part of their business secure, trusted and worry-free. Our experts will be on your side to ensure your most important resources are protected and business risks are minimized.
Incident response is the methodology used to respond and manage cyberattacks quickly to accelerate the speed of disaster recovery. Please contact us for more details.




