Managed SOC Service for More Advanced Protection
Our managed Security Operations Center (SOC) service offers advanced and extensive cybersecurity protection of your most critical IT assets, including corporate and customer data. We also simplify your path to compliance with various regulatory and vertical-specific requirements.

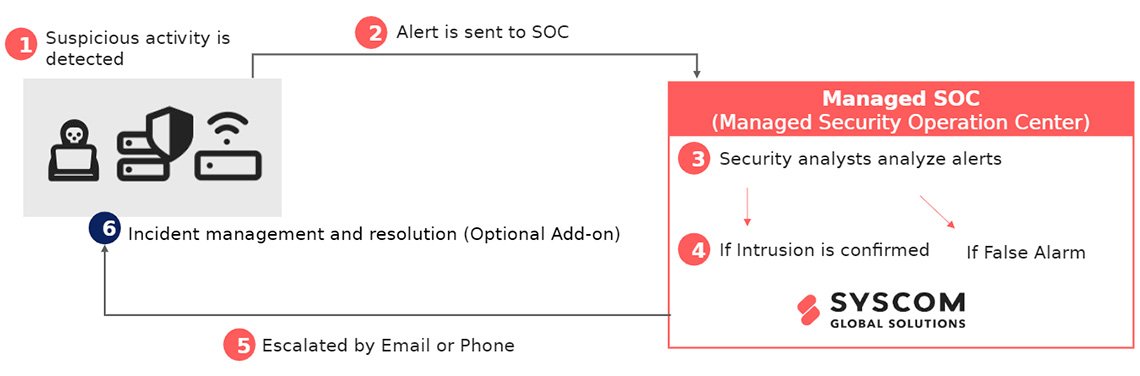
Our managed SOC Service covers from detecting suspicious activity to escalating it by email or phone (Step 1 to 5 below). Then, SYSCOM and/or Client team would execute SYSCOM’s recommendations on incident management and resolution(Step 6).
24/7 Monitoring and Analysis
Without properly managing and adopting a complete defense cycle, your SOC service or other security tools could actually hurt your business financially, while not improving cyber-defense. Our 24/7 SOC service provides a far-reaching security posture ensuring your assets and data have multiple layers of protection.

Reporting
As a part of managed SOC services, each month or quarter, we provide a detailed report containing all relevant information about your ongoing threat monitoring service. It starts with a high-level assessment of your security posture all the way down to a detailed analysis of every facet of your chosen services. The information is presented as trends over four months so you can track your organization’s performance from various angles, including the number of incidents, time-to-resolution of incidents, and the overall number of vulnerabilities.

Vulnerability Assessment
Regular vulnerability assessments help analyze and uncover issues facing information systems and offer recommendations to reduce your organization’s level of risk. A vulnerability assessment usually includes the following elements:
Network infrastructure review
Vulnerability scanning, including filtering false positives
Vulnerability research
Production of a final vulnerability report
With these elements, you can:
Establish a baseline (and thus see potentially dangerous anomalies)
Track effects of patching and remediation efforts
Report to management (PCI compliance)
Identify vulnerabilities before they impact your organization

Penetration Test
Once you agree on the scope of work, we verify security weakness to determine if your organization’s data and applications will resist external attacks. In addition, we provide penetration testing on known (White Box), half-known (Gray Box), and unknown (Black Box) environments.

Testing Levels Offered:
Recognition phase
Port scanning and systems identification
Services drilling/search
Vulnerability identification and validation
Vulnerability exploitation and evaluation of associated risks
The penetration test will verify if those assets will resist hostile attacks without revealing too much information on your environment. These steps will be carried out using multiple open source tools and also specialized tools, SYSCOM will attack the systems if a potentially viable method of exploitation exists.
Protect Your Business
Comprehensive security solutions help companies of all sizes keep every part of their business secure, trusted and worry-free. Our experts will be on your side to ensure your most important resources are protected and business risks are minimized.
Our managed Security Operations Center (SOC) service offers advanced and extensive cybersecurity protection of your most critical IT assets. Please contact us for more details.




