Zero Trust Security Model (Trust No One)
The most important assets a company has are its data and its people. When compromised, intellectual property or resources can vanish in minutes, and it is not cheap. The average cost of a data breach is estimated at $3.9 million and $2.6 million for the average cost of a malware attack. IT security should always be a priority.
At SYSCOM, we protect your infrastructure, data, and people from external and internal security threats with our dynamic approach (Zero Trust Model) that addresses the unique challenges faced by every business.

Zero Trust Security
Zero Trust means as it sounds. Trust no one by default. Zero trust model is core part of our security approaches and many businesses utilize it to upgrade their security. Zero trust will always inspect and verify any device, user, network, OS and app before granting access. It is a key approach to protect businesses from external attackers and insider threats.
We adopt a Zero Trust Model to provide secure access and protect your resources.
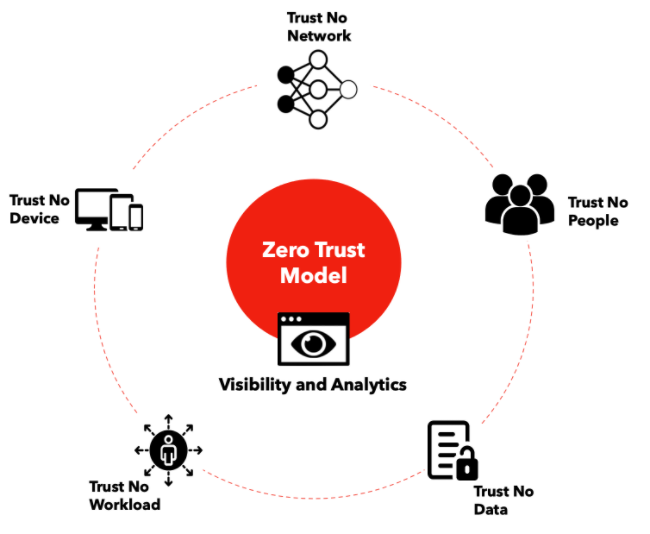
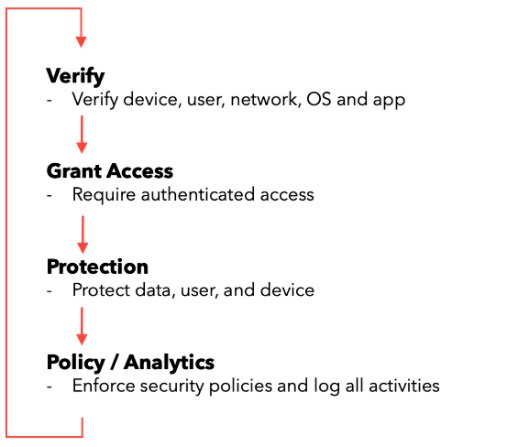
Zero Trust Security Solutions
Endpoint Security
Cloud & Web Security
Security Operation Center (SOC)
Email Security
Access Management
Vulnerability Management
Log Management
Insider Threat & User Monitoring
Protect Your Business
Comprehensive security solutions help companies of all sizes keep every part of their business secure, trusted and worry-free. Our experts will be on your side to ensure your most important resources are protected and business risks are minimized.
We help protect your infrastructure, data, and people from external and internal security threats. Please contact us for more details.
Client Stories
Finance (Asset Management): EDR & MDR Solution Case Study
SYSCOM implemented an EDR solution from CrowdStrike and setup a MDR service for detection, analysis and isolation of the cyber threats.
Finance (Global Bank): Mail Encryption and DLP Implementation Case Study
SYSCOM helped deploy an in-house virtual appliance (as an email encryption gateway) and enabled DLP at customer firewalls.



